ArmorGuard is accessed through a client side application that functions as an easy to use point and click file manager and control panel that administers all network services. Continuing developments will include: messaging, audio, video, database functionality and supporting hardware that will provide the infrastructure for a host of value added developments, and strategic partner integrations.
of file sharing and communications network application for Windows
for Windows
ArmorGuard is accessed through a client side application that functions as an easy to use point and click file manager and control panel that administers all network services. With development this initial network application will be upgraded to include: messaging, audio, video, database functionality and supporting hardware that will provide the infrastructure for a host of value added developments, and strategic partner integrations.
Why is ArmorGuard So Special?
How It Works.
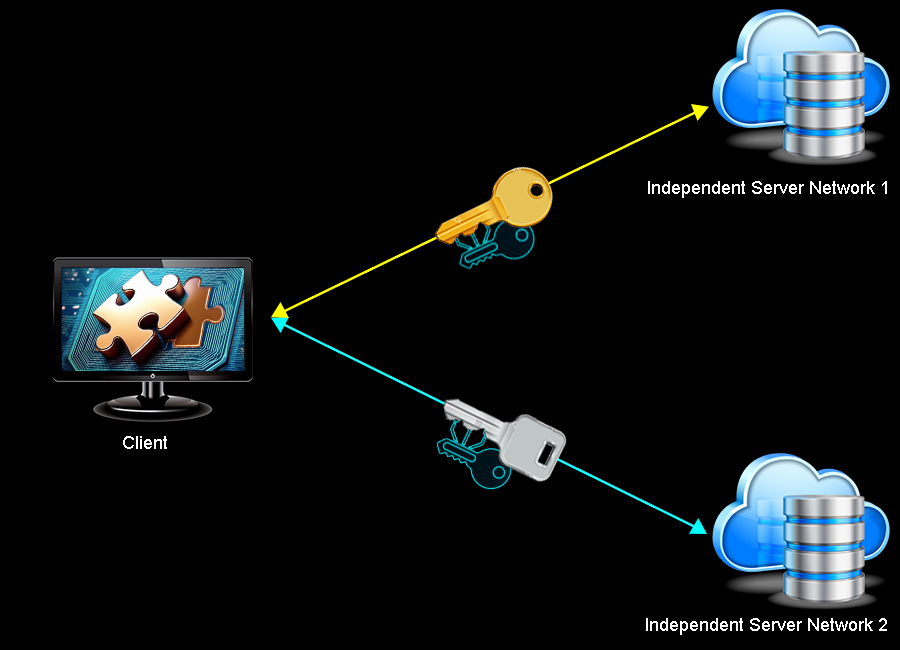
Two Independent Server Clouds
First Line of Defense
ArmorGuard distinguishes itself by operating two completely autonomous server network clouds, a primary cloud network, and a secondary cloud network.
Each message’s content is subdivided into a series of subblock puzzle pieces that place some portion of the message on a primary network and the remaining portion on an independent secondary network, never placing all of a message’s subdivided pieces in any one place.
Cipher Keys Independently Generated
By Two Autonomous Cloud Networks
Second Line of Defense
ArmorGuard independently produces two key sets. Each set is produced independently of the other set, in a process that precludes unauthorized parties including JumPedal, from ever having both keys.
- Message transmission or storage is initiated by a client request for network authorization, which creates two keys, one created by the network’s primary cloud network and one by a secondary cloud network.
- When a client sends a message, ArmorGuard’s independent cloud servers transmit its key sets to the client system for key cross checking encoding and decoding authorization, Interweave or One-Time Pad key assembly and message encoding.
Each Independently Generated Key Contains a Hidden Hardware Deadbolt Authorization Key
Third Line of Defense
Two keys each generated on an independent network, each with an embedded-hidden deadbolt authorization creates four interdependent key authorizations that are performed at network end-points before a final Interweave, or One-Time Pad, (OTP) key can be assembled for message encoding.
ArmorGuard contains a unique system of cross-locking dependencies that require multiple authorizations. Each key set with an embedded-hidden authorization, will be transmitted to a client’s device where the four key parts are cross validated, and then assembled into a single final key for message ciphering.
- ArmorGuard’s two key sets and two embedded-hidden deadbolt authorizations produce a complicated system of cross-linked relationships that divides each message’s keys into four parts, two visible and two hidden and delivers these keys by two different networks.
- It is an impossible system for any hacker to approach. Where are the keys and how do they find them when they are in two different places? How do they uncover the hidden keys, and if they are lucky enough to do that, how do they reassemble them into an assembled key?
- With the introduction of paired InfinityCoil and CipherCoil microchips, ArmorGuard’s initial four key release will be transformed into a hardware protected quantum secure cross locked system.
Nested key-in-a-key cross checks give you full control of your information, as you are the only person with the with the end-point device that can assemble the keys that are required to decode a message.
One-After Another Encryption Cascade
Fourth Line of Defense, Applies Six Uniquely Layered Ciphers
Once the cipher keys have been delivered to a client application and a final message key assembled from its four parts, message ciphering begins applying one on top of another layered application of the following listed ciphers.- XOR CIPHER
XOR ciphering (pronounced “ZOR”) is a very effective, though commonly applied cipher. ArmorGuard utilizes the XOR cipher to randomize input messages. - SUBBLOCK DIVISION OF INFORMATION
Randomized messages are subdivided into fixed bit length packets and randomly assigned alpha-numeric identifiers that remove any relationship to the original message name. - RANDOM NOISE INSERTION
Random noise is inserted into each of a message’s subblocks in a process that adds complexity to the message’s ciphering. - INTERWEAVE INDEX MODULATORS
The bit indexes of each of a message’s subblocks are scrambled. Scrambling is accomplished by unique index scrambling methods, each with their own indexing arrangement. - ONE-TIME PAD
The perfect One-Time Pad cipher is encoded into each individual subblock. - STATISTICALLY UNIFORM STORAGE TERMINAL
 Having completed ciphering, encrypted subblocks are placed into a data terminal for storage and transmission. Each terminal contains millions of similar bit length ciphered subblocks, each within a randomized alpha-numeric identifier. All virtually identical in their randomized structure, and naming conventions that make it impossible for a hacker to know how many and which of millions of subblocks create a message.
Having completed ciphering, encrypted subblocks are placed into a data terminal for storage and transmission. Each terminal contains millions of similar bit length ciphered subblocks, each within a randomized alpha-numeric identifier. All virtually identical in their randomized structure, and naming conventions that make it impossible for a hacker to know how many and which of millions of subblocks create a message.
Performance Reporting
the cipher complexity of the network’s cipher-randomizations
and their performance metrics.
- ArmorGuard’s four lines of defense, six ciphering methods, and supporting systems make hacking of JumPedal’s technology a next-to-impossible proposition.
- ArmorGuard’s initial software products are quantum-safe technologies which are unhackable today. With the addition of InfinityCoil and CipherCoil Microchips, ArmorGuard will be upgraded to a quantum-secure technology, which is never hackable by any method, irrespective of available time or computing power.
- How is quantum-safe vs. quantum-secure measured? It comes down to the ciphers that are applied to encoding a message. JumPedal provides lengthy evaluation reports that contain before and after ciphering metrics, as well as charts and graphs that describe the levels of randomness achieved in ciphering. We have included some of these reports for your review .
Two Independent Server Clouds
First Line of Defense
ArmorGuard distinguishes itself by operating two completely autonomous server network clouds, a primary network cloud, and a secondary network cloud.
Each message’s content is subdivided into a series of subblock puzzle pieces that place some portion of the message on a primary network and the remaining portion on an independent secondary network, never placing all of a message’s subdivided pieces in any one place.
Cipher Keys Independently Generated
By Two Autonomous Cloud Networks
Second Line of Defense
ArmorGuard independently produces two key sets. Each set is produced independently of the other set, in a process that precludes unauthorized parties including JumPedal, from ever having both keys.
- Message transmission or storage is initiated by a client request for network authorization, which creates two keys, one created by the network’s primary cloud network and one by a secondary cloud network.
- When a client sends a message, ArmorGuard’s independent cloud servers transmit its key sets to the client system for key cross checking encoding and decoding authorization, Interweave or One-Time Pad key assembly and message encoding.
Each Independently Generated Key Contains a Hidden Hardware Deadbolt Authorization Key
Third Line of Defense
Two keys each generated on an independent network, each with an embedded-hidden deadbolt authorization creates four interdependent key authorizations that are performed at network end-points before a final Interweave, or One-Time Pad, (OTP) key can be assembled for message encoding.
ArmorGuard contains a unique system of cross-locking dependencies that require multiple authorizations. Each key set with an embedded-hidden authorization, will be transmitted to a client’s device where the four key parts are cross validated, and then assembled into a single final key for message ciphering.
- ArmorGuard’s two key sets and two embedded-hidden deadbolt authorizations produce a complicated system of cross-linked relationships that divides each message’s keys into four parts, two visible and two hidden and delivers these keys by two different networks.
- It is an impossible system for any hacker to approach. Where are the keys and how do they find them when they are in two different places? How do they uncover the hidden keys, and if they are lucky enough to do that, how do they reassemble them into an assembled key?
- With the introduction of paired InfinityCoil and CipherCoil microchips, ArmorGuard’s initial four key release will be transformed into a hardware protected quantum secure cross locked system.

Nested key-in-a-key cross checks give you full control of your information, as you are the only person with the with the end-point device that can assemble the keys that are required to decode a message.
One-After Another Encryption Cascade
Fourth Line of Defense, Applies Six Uniquely Layered Ciphers
Once the cipher keys have been delivered to a client application and a final message key assembled from its four parts, message ciphering begins applying one on top of another layered application of the following listed ciphers.
- XOR CIPHER
XOR ciphering (pronounced “ZOR”) is a very effective, though commonly applied cipher. ArmorGuard utilizes the XOR cipher to randomize input messages. - SUBBLOCK DIVISION OF INFORMATION
Randomized messages are subdivided into fixed bit length packets and randomly assigned alpha-numeric identifiers that remove any relationship to the original message name. - RANDOM NOISE INSERTION
Random noise is inserted into each of a message’s subblocks in a process that adds complexity to the message’s ciphering. - INTERWEAVE INDEX MODULATORS
The bit indexes of each of a message’s subblocks are scrambled. Scrambling is accomplished by unique index scrambling methods, each with their own indexing arrangement. - ONE-TIME PAD
The perfect One-Time Pad cipher is encoded into each individual subblock. - STATISTICALLY UNIFORM STORAGE TERMINAL
 Having completed ciphering, encrypted subblocks are placed into a data terminal for storage and transmission. Each terminal contains millions of similar bit length ciphered subblocks, each within a randomized alpha-numeric identifier. All virtually identical in their randomized structure, and naming conventions that make it impossible for a hacker to know how many and which of millions of subblocks create a message.
Having completed ciphering, encrypted subblocks are placed into a data terminal for storage and transmission. Each terminal contains millions of similar bit length ciphered subblocks, each within a randomized alpha-numeric identifier. All virtually identical in their randomized structure, and naming conventions that make it impossible for a hacker to know how many and which of millions of subblocks create a message.
Performance Reporting
the cipher complexity of the network’s cipher-randomizations
and their performance metrics.
- ArmorGuard’s four lines of defense, six ciphering methods, and supporting systems make hacking of JumPedal’s technology a next-to-impossible proposition.
- ArmorGuard’s initial software products are quantum-safe technologies which are unhackable today. With the addition of InfinityCoil and CipherCoil Microchips, ArmorGuard will be upgraded to a quantum-secure technology, which is never hackable by any method, irrespective of available time or computing power.
- How is quantum-safe vs. quantum-secure measured? It comes down to the ciphers that are applied to encoding a message. Jumpedal provides lengthy evaluation reports that contain before and after ciphering metrics, as well as charts and graphs that describe the levels of randomness achieved in ciphering. We have included some of these reports for your review .
